Phishing Emails Sent to Dickinson Accounts over Summer
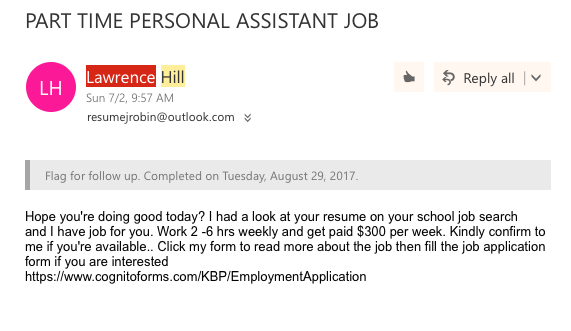
An example of a fraudulent email sent to a student’s Dickinson account over the summer.
This past summer, the Dickinson College email system was attacked by several hackers intending to collect personal information, including usernames and passwords, and gain access to secure accounts such as Gateway and Self Service Banner.
Emails included subject lines such as “Personal Assistant Position Available!” and “Microsoft Important Notice.” Some of these emails appeared to be from Dickinson employees or offices, whereas others advertised a job position for students.
Hackers may intend to sell the gathered information, attempt to access other accounts belonging to the person or use the affected account to send further fraudulent emails. “This is a big money industry,” said Andrew Connell, director of user services, on the practice of sending these emails, or “phishing.”
The college currently maintains a firewall to block fraudulent emails. However, this system is reactive; it can only catch threats it has previously encountered. Robert Renaud, vice president and chief information officer said:
“Unfortunately, this phishing and fraudulent email function is a very reactive function…There’s nothing we can do to 100% stop this.”
Dickinson maintains a second firewall, which is able to block malicious links. If the second firewall catches a malicious link in an email, it will redirect anyone who clicks the link away from the malicious website. However, each link must be entered into this firewall manually.
Since many Dickinson email addresses are publicly displayed, the hackers were able to tailor their emails. Through a process known as “spoofing,” they created false email addresses in the names of real Dickinson faculty, staff and officers, allowing the emails to appear legitimate.
Part of the reason behind the attack was the college’s public switch to Office 365, according to Connell.
For students who have clicked links or replied to the emails, Kevin Truman, director of infrastructure services and information security, advised:
“Change your password and you’re fine. If you don’t know who it’s from, and if they’re asking for passwords [and] username information, that is never going to be a valid email.”
Dickinson has launched a website, www.dickinson.edu/phishingalerts, to display screenshots of fake emails. Students are also free to contact the library help desk with any questions.





